Get IT on Target
Business leaders know that scaling growth takes more than ambition — it requires alignment, control, and confidence in the systems that support the business. We’ve helped mid-sized organizations navigate transformation and risk-aligned modernization. Along the way, we consistently encounter the same barriers: unresolved technical debt, escalating IT costs, competing priorities, limited internal capacity, and a lack of trust in the technology strategy to drive growth, compliance, and resilience.
Our Strategic Assessments follow our proven 5-step process designed to evaluate your IT and cybersecurity posture. It delivers a clear picture of your current state, benchmarks of control maturity, a future-state risk-aligned vision, and a prioritized roadmap for remediation, compliance readiness, and cyber insurability. The outcome: actionable insight that strengthens decision-making and positions IT and cyber as strategic enablers of performance, protection, and progress.
Align IT for Long-Term Resilience, Performance, and Growth.
Why is a Strategic Assessment important for your business?
Conducting a comprehensive assessment is a strategic investment in understanding the health of your IT environment, control landscape, and process capabilities. Our Strategic Assessments help organizations align technology with business goals, enhance cyber risk awareness, and build confidence in decision-making. It provides a clear view of IT and cybersecurity maturity — forming the foundation for risk-informed planning, compliance readiness, and growth-focused transformation.
Key benefits of this due diligence process include:
 Growth Enabler: A Strategic Assessment delivers the critical insight needed to align your IT and cybersecurity strategy with business growth objectives. It provides assurance that your infrastructure, controls, and capabilities can scale effectively — reducing friction, avoiding costly missteps, and supporting sustainable, optimized operations.
Growth Enabler: A Strategic Assessment delivers the critical insight needed to align your IT and cybersecurity strategy with business growth objectives. It provides assurance that your infrastructure, controls, and capabilities can scale effectively — reducing friction, avoiding costly missteps, and supporting sustainable, optimized operations.
 Risk Mitigation: Establish a clear view of your current vulnerabilities and overall cyber risk posture, supported by an actionable roadmap to strengthen controls and reduce exposure. This enables proactive protection against breaches, data loss, and system failures — driving effective risk mitigation and enhancing organizational resilience.
Risk Mitigation: Establish a clear view of your current vulnerabilities and overall cyber risk posture, supported by an actionable roadmap to strengthen controls and reduce exposure. This enables proactive protection against breaches, data loss, and system failures — driving effective risk mitigation and enhancing organizational resilience.
 Cost Optimization: Improve the cost-effectiveness of your IT environment, identifying opportunities to streamline operations and optimize IT resource allocation, resulting in potential cost savings and improved financial performance.
Cost Optimization: Improve the cost-effectiveness of your IT environment, identifying opportunities to streamline operations and optimize IT resource allocation, resulting in potential cost savings and improved financial performance.
 Increase ROI: Maximize return on IT-enabled investments by improving visibility, governance, and utilization of existing assets. Strengthened controls and accountability frameworks support smarter prioritization, better project execution, and measurable value realization from your technology portfolio.
Increase ROI: Maximize return on IT-enabled investments by improving visibility, governance, and utilization of existing assets. Strengthened controls and accountability frameworks support smarter prioritization, better project execution, and measurable value realization from your technology portfolio.
 Stakeholder Confidence: A clear understanding of your risk posture, improvement opportunities, and actionable next steps gives stakeholders — including clients, investors, insurers, and partners — greater assurance in your organization’s ability to identify, manage, and reduce cyber risk with intention and accountability.
Stakeholder Confidence: A clear understanding of your risk posture, improvement opportunities, and actionable next steps gives stakeholders — including clients, investors, insurers, and partners — greater assurance in your organization’s ability to identify, manage, and reduce cyber risk with intention and accountability.
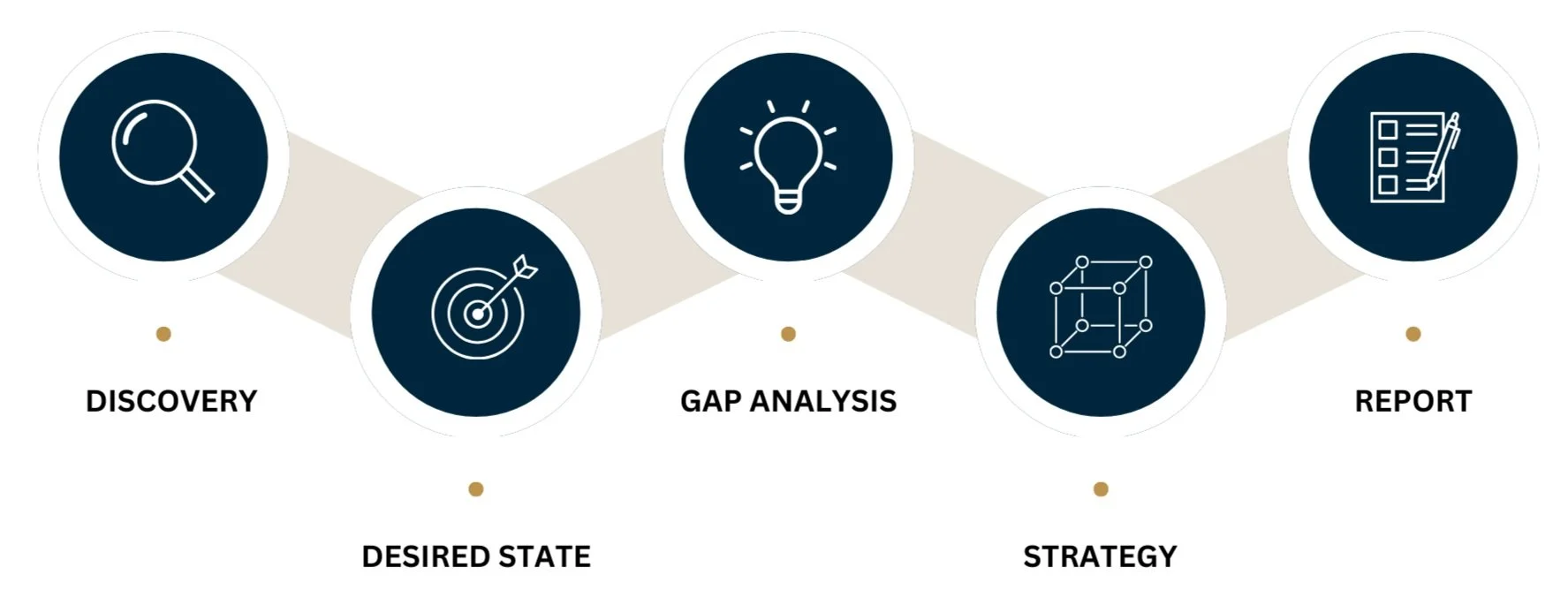
Our Proven 5-Step Assessment Process
Our expert-led 5-step assessment process is built to thoroughly evaluate your organization’s current IT environment, cyber risk posture, and control maturity. This structured approach uncovers performance gaps, operational risks, and growth opportunities aligned with future business demands. It delivers critical insights into IT health, processes, technologies, and effectiveness — supported by both qualitative and quantitative evaluations. The result is a clear, actionable roadmap that aligns IT capabilities with business objectives, enabling informed decisions and measurable improvements.
Our Strategic Assessments are designed to establish a baseline across key areas such as security posture, IT maturity, cyber risk, and strategic alignment — uncovering performance gaps and providing clear, actionable recommendations to improve control effectiveness and business resilience.
We offer both rapid one-day assessments for organizations seeking fast, boardroom or insurer ready reporting, high-level insights with minimal disruption, as well as comprehensive assessments, typically delivered over 2 to 3 weeks, which culminate in a detailed, actionable strategic roadmap tailored to your business objectives. Engagements are scoped based on infrastructure complexity and stakeholder involvement, and all are delivered with a focus on efficiency, clarity, and measurable value.
1.Discovery
The assessment begins with an information request to provide a comprehensive set of documentation and completed questionnaires from key areas of the business, including your technical team(s). This background is key for our team to gain a full understanding of the current state of your IT environment and related services. If any documentation or information isn’t available or current, the topic can be addressed in the in-depth interviews.
-
For full transparency in support of your comprehensive assessment, documentation and IT information requests may include:
• Technology asset inventory
• Current IT policies and procedures (if any) including, but not limited to: incident response plan, disaster recovery plan, and IT security policies.
• Most recent IT operational reporting package / KPIs inc. uptime, systems health, cybersecurity
• Any recent cyber incidents or major outage information including post-incident review reports
Stakeholder Interviews
Throughout this process, we’ll engage in a series of interviews involving key stakeholders and leadership to gain an in-depth understanding of business goals and operational intricacies. A well-organized interview schedule typically explores subjects such as:
• Company background, history, expertise, market, key business metrics, and organizational structure
• Overview of the general technology landscape, identifying key technologies and systems you deem critical to your business operations.
• How is cybersecurity currently managed and what measures are in place to protect against cyber threats and attacks?
• Do you have established internal control measures and governance practices in place?
• Current priorities for technology and known desires not realized current IT environment.
2.Desired State
Upon thorough analysis of the documentation and insights garnered through the discovery phase, the assessment team will craft a future envisioned technology state and business goals objectives. This desired state delineates the existing technological landscape where the issue(s) manifests and its impact on overall business operations and company finances.
-
The structured format guiding the definition of the desired state includes:
• A description of the current state, highlighting growth inhibitors or pain points that act as barriers to growth.
• Business strategic drivers derived from key executive stakeholder interviews.
• A vision for future IT landscape following strategic investment.
• Preliminary recommendations and suggestions for strategic improvements to set you on the path to resiliency and growth enablement.
3.Gap Analysis
Using the findings outlined in the ‘Desired State’, as well as the known business goals acquired through Discovery, the assessment team will conduct an in-depth gap analysis to thoroughly evaluate your existing IT technology stack and line of business applications. This comprehensive review encompasses organizational team structure, overall network architecture, as well as controls and governance mechanisms.
4.Strategy
Following the thorough evaluation of current state tools, technology and operational processes, we’re able to identify gaps and inefficiencies. Measured against your business goals and industry best practices, the gap analysis illuminates recommended remedies and strategic growth enablers. The clarity provided empowers informed decision-making in the prioritization of transformation initiatives to move your organization from current state to desired state.
5.Report & Debrief
Upon completion, you will be presented with a comprehensive report tailored to your organization’s goals and leadership decision-making. A live review is conducted with key stakeholders to review findings uncovered in the assessment and provides an opportunity to openly discuss significant insights, expand on recommendations, gather additional feedback and deliberate on the cost benefit of proposed initiatives. Following the debriefing, the report undergoes finalization, integrating final thoughts and inputs and refining the strategic roadmap.
When is it time to conduct a strategic IT assessment?
Technology is constantly changing which brings numerous benefits as well as increased risks. While ideally, proactive and ongoing, at a minimum, periodic and independent reviews of your technology environment will allow you to track progress and ensure you remain competitive and aligned with the evolving needs and goals of your business. Business drivers which triggers a need for a strategic IT assessment include:
Planning significant business growth or change
Considering an enterprise resource planning “ERP” system
A major IT outage or cybersecurity breach
Exploring M&A opportunities
Preparing to go public
Establishing a performance baseline for continuous improvement
What should you expect during a Strategic Assessment?
As we lead you through the IT assessment process, we take a collaborative and methodical approach. Multiple interviews are conducted with key business stakeholders to garner qualitative data to more accurately assess your experience, expectations and requirements of IT. With the goal of best positioning your organization for long-term success, it is important for everyone involved to embrace transparency and open-mindedness. We take a risk-based approach in assessing your IT environment and prioritize your critical data, systems, and related business workflows. Expect to be kept well informed of the overall assessment project status and any significant risks uncovered along the way. Any changes in schedules or roadblocks preventing timely completion will be discussed and resolved together. Our approach is one of integrity and C.A.R.E.
What are the most common findings of our Strategic Assessments?
Specific findings in final reports vary based on the scope relative to the size of the organization, but common findings include:
Low IT management process maturity prohibiting transformation enablement.
The IT architecture design is not scalable to meet the needs of the long-term business vision
The IT service delivery function does not have service level agreements in line with end user expectations
There is a lack of business continuity, disaster recovery, and cyber incident response capabilities
Business stakeholders needs have not been appropriately documented or understood
Many strategic resourcing and capability gaps can be acquired through our proprietary CyberSurance™ Programs